- Blog
#Development #QA #Testing
Project Blueprint: Quality Assurance
- 24/04/2024
Reading time 7 minutes
Microsoft has finally created an option for free HTTPS certificates in Azure App Service, that is fully managed by them. Recently announced at Ignite 2019, we can now enable HTTPS for our own domains for free on Azure App Service!
This offering differs from existing options for HTTPS in that it is missing some of the features. You can also buy App Service Certificates from Azure, which have more features than the free offering but do cost money of course.
Then there is, of course, Let’s Encrypt, which my personal blog uses. But Let’s Encrypt’s integration in Azure is not very good. It’s a bit of a mess where you kinda just hope all the components work every time to renew your certificates. I have had multiple times within the couple years that I have used it when the renewal didn’t work for one reason or another. So having a managed certificate is certainly a nice thing.
The capability is in preview, so some of these limitations may be removed. In particular, I’d like to see support for apex domains. I cannot use this feature on my blog since it is on an apex domain (joonasw.net instead of a sub-domain). A lot of applications we build for clients could use this though as those are often on sub-domains.
To test this capability, I first tried to enable it on one of my existing App Services. It already had a custom domain and an expired Let’s Encrypt certificate. The renewal had gotten broken because I moved the app to another subscription.
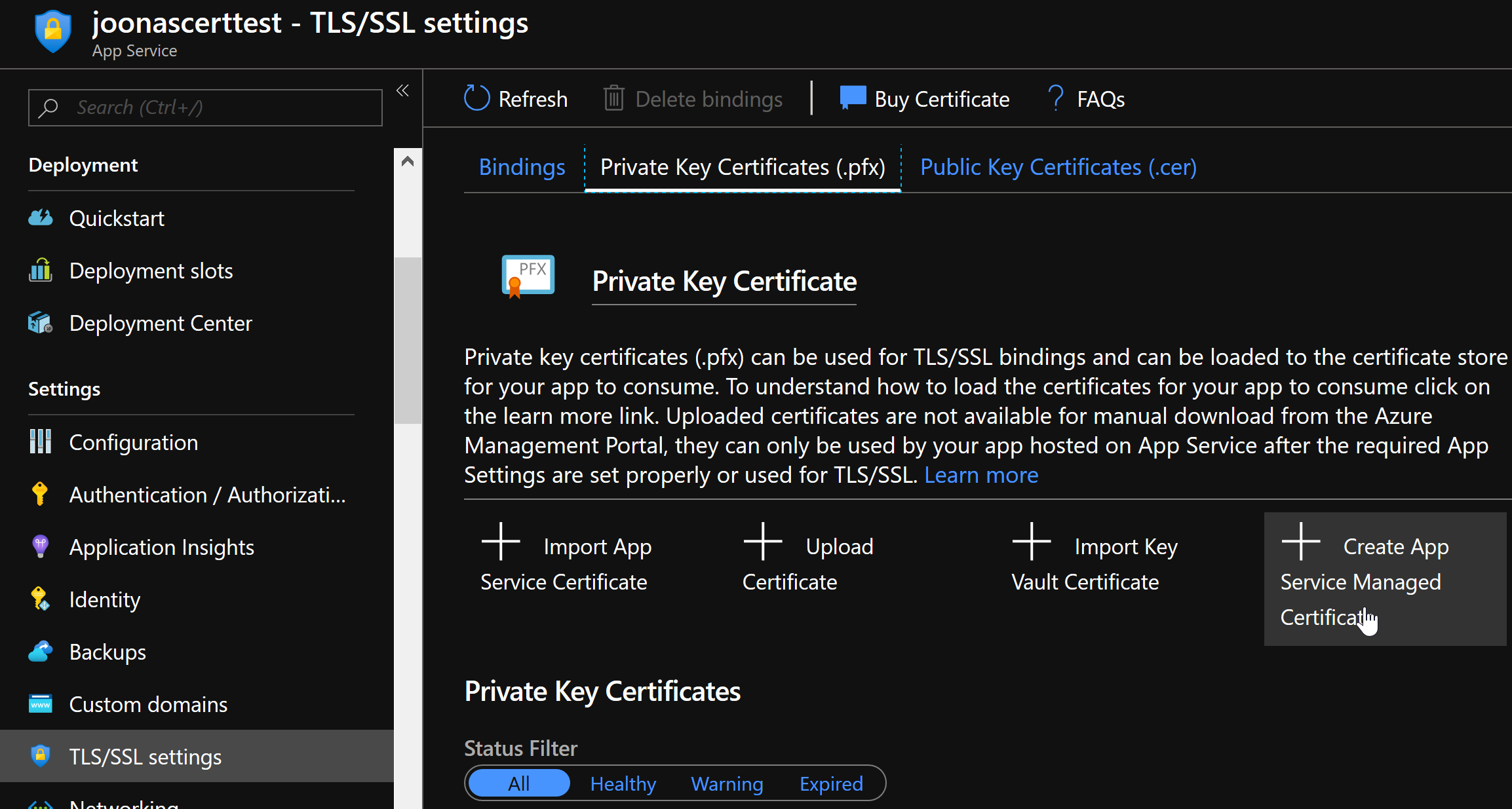
I removed the Let’s Encrypt extension, removed the existing TLS/SSL binding from the domain and went to add a certificate through the Create App Service Managed Certificate button (found under TLS/SSL settings -> Private Key Certificates).
But it did not work 🙁
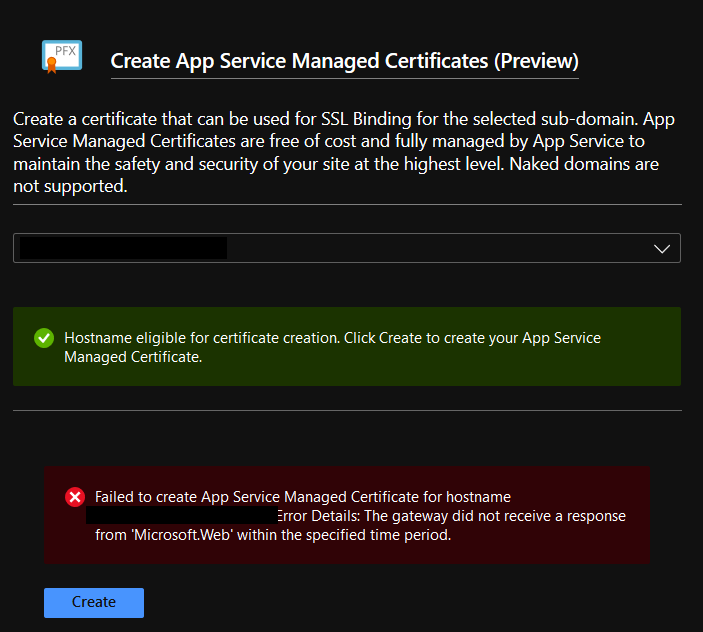
I also tried it with a new App Service, but got the same errors:
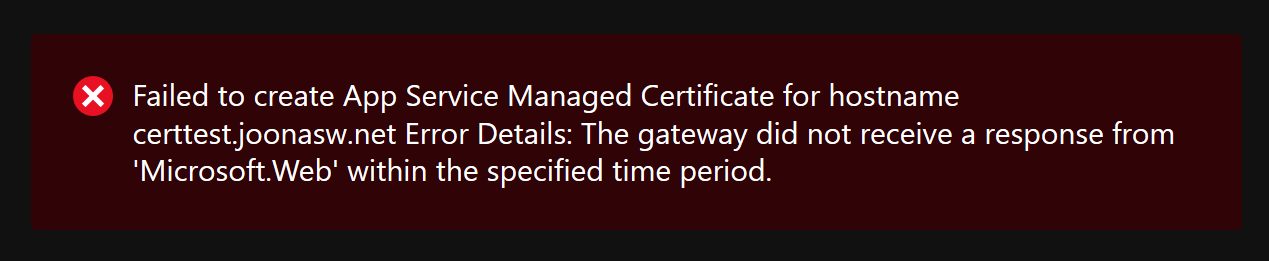
504 Gateway Timeout errors for some reason from the API. I sent a support ticket, but got notified on Twitter that the issue should be fixed the same day 🙂
So, let’s see the successful steps to adding one of these certificates:
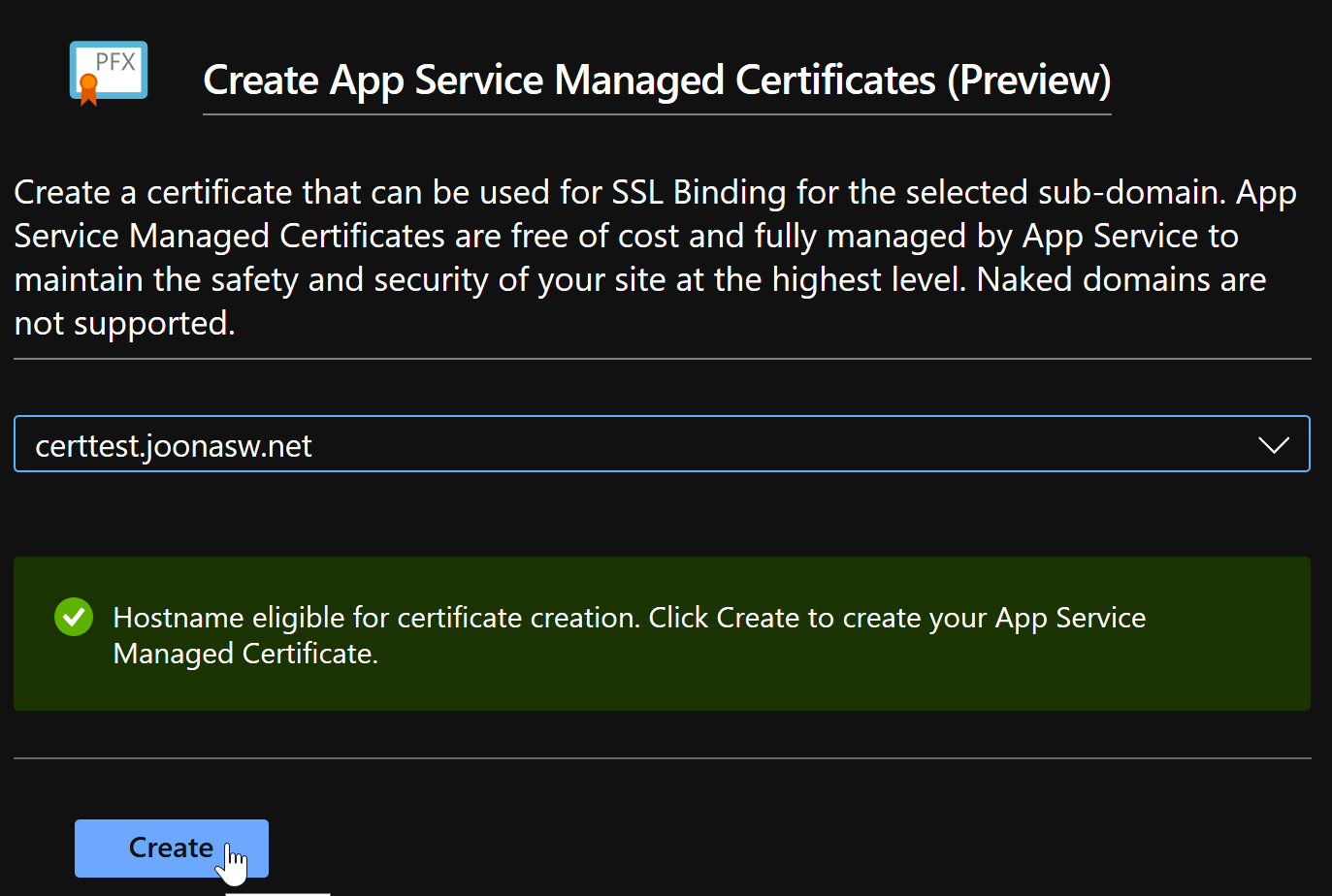
It’s pretty easy right? Just select the domain and click Create:
And done, the certificate is valid for 6 months:
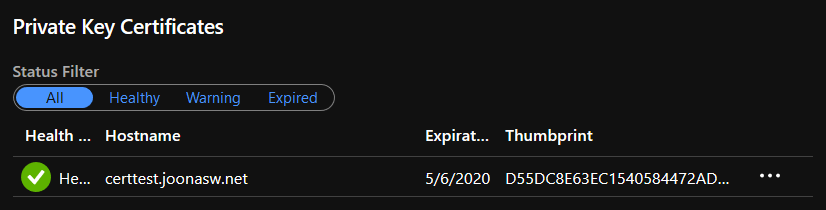
Well, almost done. Still have to add the TLS/SSL binding:
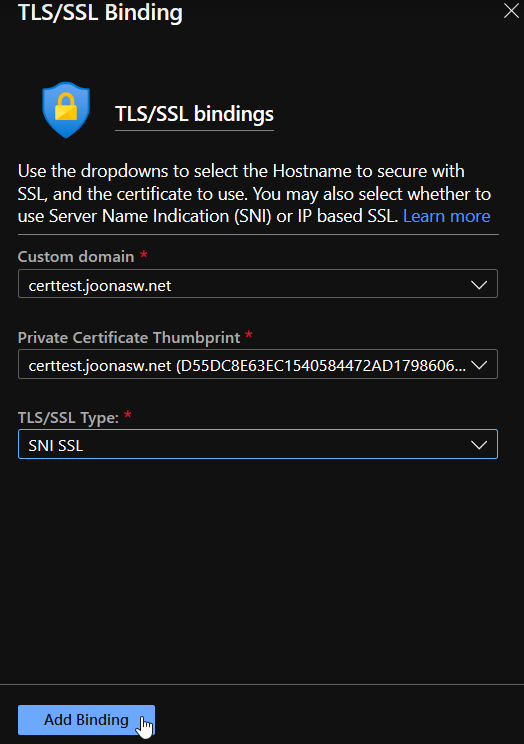
And now we are done! The certificate will be automatically renewed by Microsoft behind the scenes. Here’s the certificate chain as shown by Chrome:
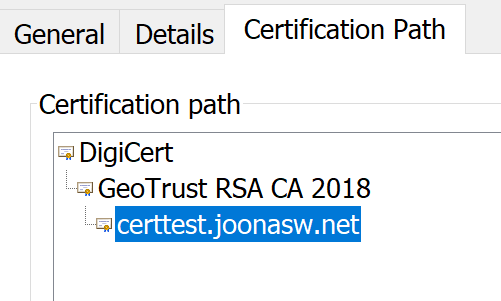
So the certificates come from DigiCert behind the scenes.
This is definitely a capability that will get used in projects later. A great step to securing the Web as well!

Our newsletters contain stuff our crew is interested in: the articles we read, Azure news, Zure job opportunities, and so forth.
Please let us know what kind of content you are most interested about. Thank you!