Imagine that your data security journey is at mid-point, and you have already started getting used to Microsoft Purview as a solution and maybe implemented some of its features in your organization’s environment. Your team is familiar with terms and solutions such as Sensitive Information Types, Data Loss Prevention (DLP) policies, Insider Risk Management, and Compliance Manager, just to name a few. You possibly have already held a few internal training sessions around Microsoft Purview as a solution and how it can be effectively utilized to achieve a higher level of compliance within your organization.
At this point, you might be wondering how to actively monitor, respond to, and mitigate potential security and compliance issues. Microsoft Purview provides robust alerting features to help organizations detect and respond to these issues. You might have a Security Operations Center (SOC) in-house or as a service from an external organization, which is responding to alerts coming in from your Azure environment. Now you are wondering if it is possible to integrate your Purview alerts into existing solutions, and whether the Security Operations personnel have enough knowledge to respond to them, or if some alerts need to be managed within the solution itself.
You don’t have to feel overwhelmed. Indeed, there are multiple sources from which Microsoft Purview can produce alerts, but I will describe these sources to you and the best practices for managing them in the most convenient manner.
Compliance Manager alerts
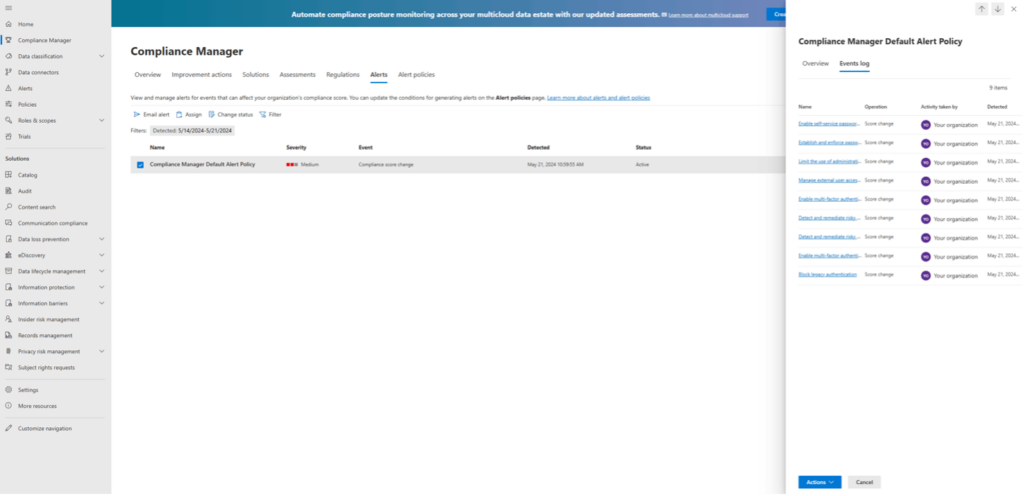
Purview’s Compliance Manager can produce alerts for various types of events so that you can stay on track with your compliance goals. You can set up alert policies, for example, when there is an increase or decrease in the compliance points awarded due to configuration changes, or when there is an assignment change for an improvement action. All of the alerts can be categorized with severity levels of low, medium, or high.
When an alert triggers, the alert recipient will receive an email when the alert policy condition is met. Then, it can be investigated on the Alerts page in Purview’s Compliance Manager itself by selecting its row in the table. Alerts are generated almost immediately after an event matching the policy’s conditions occurs.
Data Quality alerts
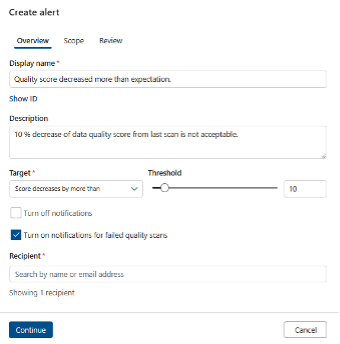
Microsoft Purview’s Unified Catalog can be configured to alert data managers if data quality scores miss expectations. Specifically, the data quality alerts will notify selected Purview users about important events or unexpected behavior detected around the quality of the data.
You can configure and set the data quality alerts in the Health Management section of the Data Quality subsection. The recommended metric is the data quality score, which requires setting up the data quality rules first. This alerting feature can be important to organizations that conduct data science activities with large datasets and utilize Microsoft Purview’s capabilities for data management. The alerts will be displayed on the Unified Catalog alerts page for further investigation.
Data Loss Prevention (DLP) alerts
Purview’s Data Loss Prevention policies can create alerts when the policy conditions are matched. DLP alerts can be categorized into two types:
- Single-event alerts
- Aggregate-event alerts
Single-event alerts mean a low volume of sensitive events has occurred. In practice, this could mean a single email has been sent outside your organization with 10 or more credit card numbers, driver’s license numbers, or social security numbers, just to name a few.
Aggregate-event alerts mean a high volume of sensitive events has occurred over a period of time (48 hours, for example). This means that 10 or more individual emails containing a single or multiple credit card numbers have been sent outside of your organization.
Data Loss Prevention alerts can be extended to cover Endpoints and Microsoft Teams when customers have chosen to use those DLP services. Before applying your DLP policies organization-wide, you can freely simulate the policies in simulation mode, which is highly recommended to ensure they work as intended.
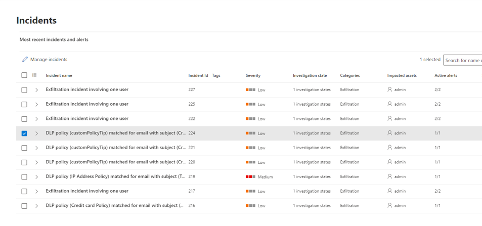
To manage and investigate DLP incidents, you can use Microsoft Defender XDR or the Microsoft Purview Compliance portal. It is highly recommended to use the Defender XDR portal for investigating incidents due to its enhanced capabilities, such as grouping incidents into an incident queue and utilizing Advanced Hunting capabilities for compliance log hunting. You can also use the Microsoft Defender XDR connector in Microsoft Sentinel to import all DLP incidents into Sentinel to extend your correlation, detection, and investigation capabilities, and to extend your automated orchestration flows using Sentinel’s SOAR capabilities.
Insider Risk Management alerts
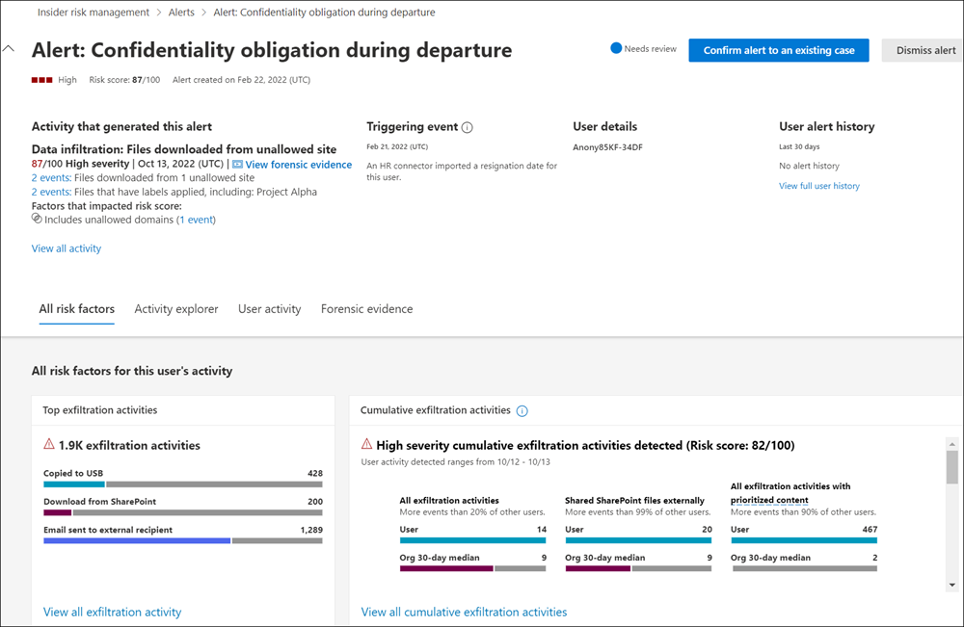
Microsoft Purview Insider Risk Management utilizes pre-defined risk indicators in Insider Risk Management policies to automatically generate alerts, providing a comprehensive overview of the current insider risk landscape. By default, policies generate alerts of varying severity (low, medium, and high), ensuring timely identification of risks. These alerts and their thresholds can be configured to align with your organizational needs.
For example, Microsoft Purview Insider Risk Management can detect potential data leakage by monitoring unusual file transfers to external locations or identify IP theft by tracking abnormal access patterns to sensitive documents. Additionally, it can flag security violations by correlating signals such as unauthorized access attempts or other relevant policy breaches.
The alerts will appear on the Alerts dashboard. Just navigate to Insider Risk Management > Reports > Alerts to view reports for generated alerts. On the dashboard, you can search alerts, view alert reports, triage them, and create an Insider Risk Management case for further investigation. You can also use Copilot to summarize alert details to help you prioritize work.
Communication Compliance alerts
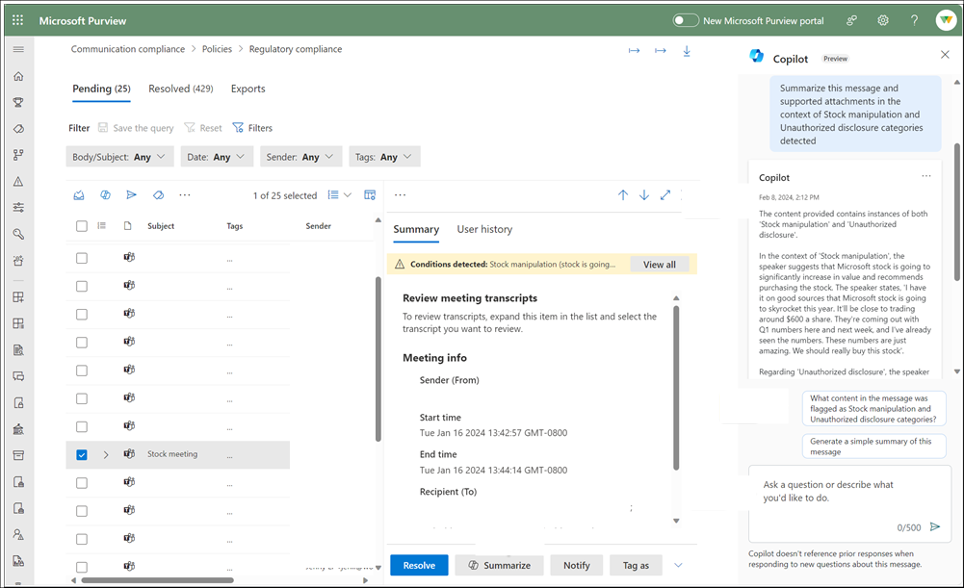
Microsoft Purview Communication Compliance helps organizations follow rules and spot problems like sharing private company information, using harmful language, or sharing inappropriate content. It keeps user privacy safe by hiding usernames, allowing only certain people to access information, and keeping records of who does what.
Even though Communication Compliance policies are not very commonly used in Finland, like DLP policies, Communication Compliance policies produce alerts for message issues that match your policy conditions. After receiving your first alert, you can quickly remediate it in Communication Compliance > Alerts dashboard. This alerting feature uses sensitive info types, keyword lists, and regulatory trainable classifiers to detect unallowed content in Teams messaging, for example. Trainable classifiers can be used to detect activities such as corporate sabotage, money laundering, stock manipulation, and unauthorized disclosure.
Conclusion
Microsoft Purview alerting features are developed to help you detect, respond to, and remediate a vast array of compliance violations that may occur in your organization. With clear roles, working procedures, and relevant personnel in place for remediation, you can swiftly coordinate corrective actions and prevent such activities from happening in the future. It is crucial to keep your organization’s employees aware of such technologies to enforce your compliance requirements and prevent violations before they are even detected by the policies mentioned above. You don’t necessarily need all of these alerting policies to be active to start protecting your data assets. You can start with the areas that are most vital to your organization and create a continuous development roadmap for the future to expand policy coverage step-by-step. This approach is recommended so that your compliance personnel have enough know-how to respond to these alerts.
How to get started?
We suggest starting with a workshop, either with Microsoft or your dedicated Microsoft partner, and including relevant stakeholders from your company. This workshop should map out responsibilities, define how you should identify your data, and start the relevant governance and data security actions. This workshop includes clear and precise guidance for enabling relevant alerting functionalities of Microsoft Purview tailored especially for your organization. The workshop outlines the steps to get started with implementing Microsoft Purview and protecting your organization against data security risks.


