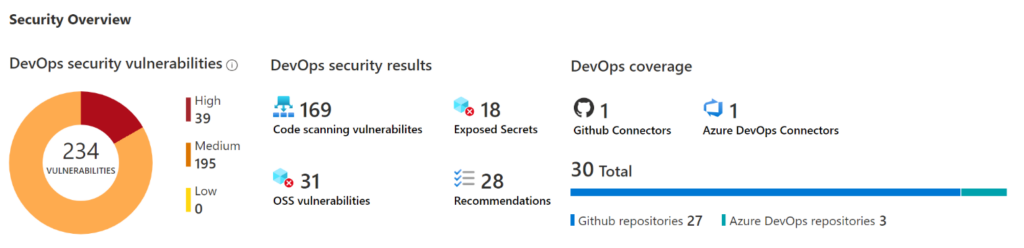
In this blog, I won’t be discussing the overall importance of integrating security into DevOps workflows. Instead, I will focus on the recent changes and how Microsoft Defender CSPM has been updated with capabilities to integrate the solution with yor CI/CD pipelines. By doing so, you can detect vulnerabilities before implementation, prevent security bottlenecks, and maintain compliance and protection across cloud platforms like Microsoft Azure, Amazon AWS, and Google GCP.
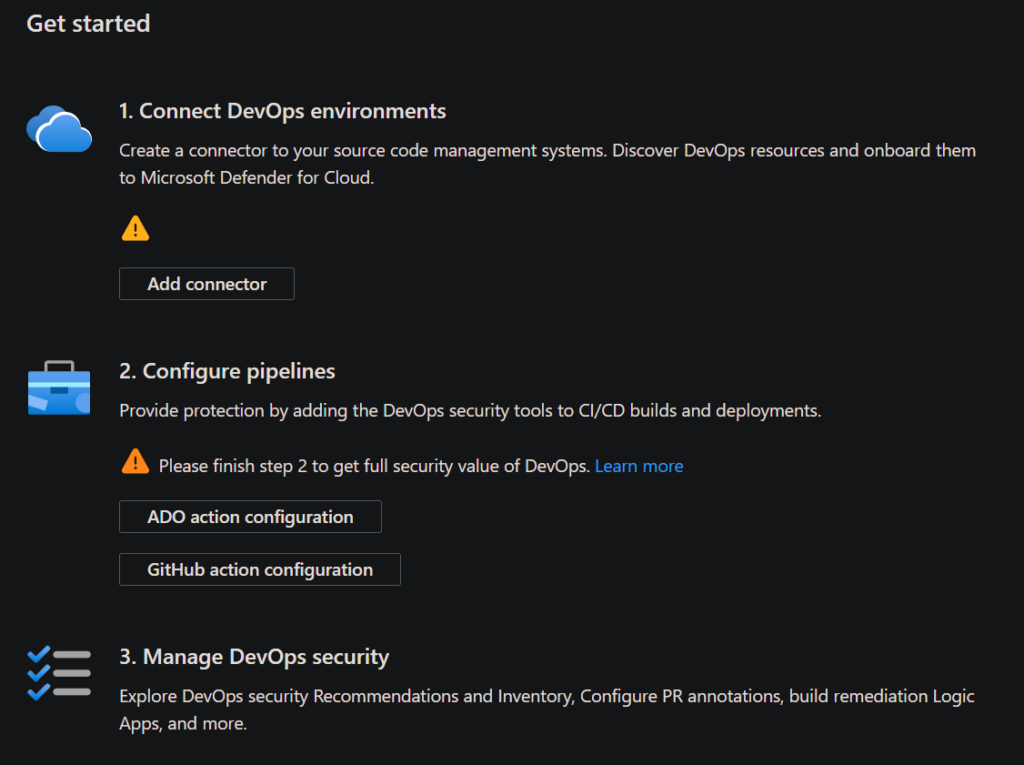
How Defender CSPM helps you establish DevSecOps practices
Shift-Left Security -mindset
Defender CSPM scans for vulnerabilities and misconfigurations early in the SDLC, detecting issues in code or Infrastructure-as-Code (IaC) templates before they reach production. By shifting security to the left, teams can identify and address potential threats during the development phase, reducing the risk of vulnerabilities making it to production. This proactive approach not only enhances security but also saves time and resources by catching issues early.
Code-to-Cloud Contextualization
Defender CSPM provides end-to-end visibility from code to cloud, tracing vulnerabilities from the development phase through deployment. For instance, if a developer implements an insecure dependency, Defender CSPM can assess its impact on the cloud environment, enabling teams to address security risks in context. This holistic view ensures that security measures are comprehensive and effective, covering the entire lifecycle of the application.
Infrastructure-as-Code (IaC) Security
By analyzing Terraform, ARM, and other IaC templates, Defender CSPM helps prevent security misconfigurations before infrastructure is complete. If a Terraform script inadvertently exposes a storage bucket to the internet, Defender CSPM flags the issue and provides practical remediation steps. This proactive analysis ensures that infrastructure is secure from the moment it is deployed, reducing the risk of misconfigurations leading to security breaches.
Reachability Analysis (via Endor Labs Integration)
Through integration with Endor Labs, Defender CSPM can perform advanced reachability analysis on vulnerabilities within code dependencies or container images. By identifying whether your application actually calls the affected functions or libraries, this approach helps application security teams focus remediation efforts on realistically exploitable vulnerabilities—reducing noise and prioritizing the highest-impact risks. This targeted approach ensures that security efforts are efficient and effective.
Continuous Security Assessments
Rather than relying on periodic audits, Defender CSPM continuously monitors resources to identify and address misconfigurations, vulnerabilities, and compliance issues in near real-time. This continuous assessment ensures that security is up-to-date and that potential issues are addressed promptly, maintaining a strong security posture at all times.
Container Image Security
Defender CSPM scans container images for known vulnerabilities before deployment, alerting development teams if an exploitable package is included and providing guidance for mitigation. This ensures that containerized applications are secure from the start, reducing the risk of vulnerabilities being introduced into the production environment. However, this does not exclude the need for regular patching of the container images.
Security as Code
Security policies, governance models, and compliance requirements can be codified and enforced automatically within CI/CD pipelines, allowing teams to integrate security without disrupting delivery speed. This approach ensures that security is an integral part of the development process, rather than an afterthought, and that compliance is maintained consistently during the development process.
Automated Remediation
Customizable playbooks can automatically fix issues—from misconfigured IAM policies to security patches—reducing manual effort and human error. This automation ensures that security issues are addressed quickly and efficiently, minimizing the risk of human error and freeing up development teams to focus on other tasks.
Security Gates in CI/CD Pipelines
To prevent insecure deployments, Defender CSPM enforces security gates in DevOps workflows. If a high-risk vulnerability is detected during the build or deployment phase, the pipeline is halted until the issue is resolved, ensuring only secure code reaches production. This ensures that security is maintained throughout the development process and that vulnerabilities are addressed before they can cause harm.
Seamless Integration with DevOps Workflows
Defender CSPM integrates natively into popular CI/CD solutions, enabling collaborative workflows that bring together development, security, and operations teams under a shared responsibility model. This integration ensures that security is a collaborative effort and that all teams are working together to maintain a secure environment.
Automated Compliance Checks
Defender CSPM verifies infrastructure and applications against regulatory standards (e.g., PCI-DSS, HIPAA) throughout the DevOps lifecycle. New compliance requirements (e.g., mandatory data encryption) are continuously evaluated for adherence. This ensures that compliance is maintained consistently and that new requirements are addressed promptly.
Continuous Visibility and Risk Prioritization
Defender CSPM's dynamic security posture assessment helps teams focus on high-impact risks by surfacing critical vulnerabilities with remediation guidance. This ensures that security efforts are focused on the most important issues and that vulnerabilities are addressed in a timely and effective manner.
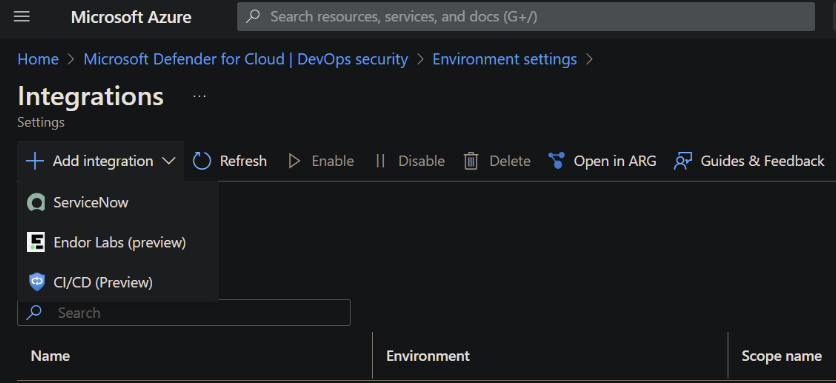
Conclusion
Integrating security into DevOps is no longer a daunting task that requires third-party solutions or implementing Defender for DevOps or GitHub Advanced Security. By utilizing CSPM’s integration capabilities, you can easily automate security gates to reduce the risk of vulnerabilities and maintain a more secure application production environment. The technical implementation is quite straightforward and does not require significant effort—only the necessary user roles and, of course, approval from management.